Essential Eight
As we move into 2024, cybersecurity is the most pressing issue facing Australian businesses that find themselves grappling with a range of cybersecurity challenges. Organisations in both the public and private sector find themselves confronted, with security threats coming at them from every angle. From increasingly sophisticated phishing attacks to internal web address hijacking and evolving ransomware threats, the imperative for robust defence mechanisms is clear.
To enhance cybersecurity resilience, the Australian government has now mandated Essential Eight (E8) compliance for government entities. And forward-thinking executives in the private sector are quickly following suit to protect their assets, up their maturity levels and fortify their security posture.
Origin and Adoption of the Essential Eight Framework
Developed by the ACSC in 2017, the Essential Eight was originally designed to enhance security and operational practices within Australian government agencies, departments, local councils, and public sector businesses. However, the Essential Eight is now gaining traction among private businesses that understand it is a valuable starting point for evaluating security controls and establishing a baseline in cyber security.
The Essential Eight encompasses eight critical areas, each addressing distinct aspects of cyber security. It is routinely updated to keep pace with the constantly evolving nature of threats in the cyber security landscape. The eight areas are divided into three primary objectives - preventing attacks, limiting the impact of attacks, and data recovery and availability.
Deciphering the Essential Eight Maturity Levels
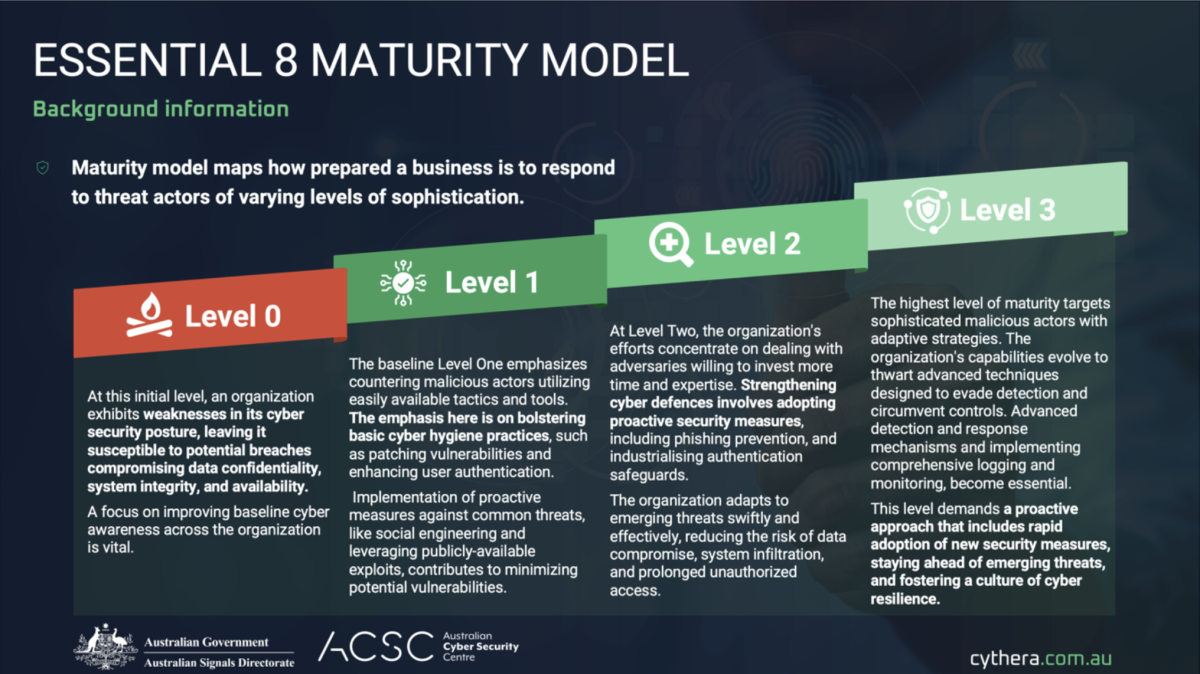
The three levels of maturity within the Essential Eight (E8) framework are designed to help organisations track their cybersecurity posture based on their specific needs and the nature of the threats they face.
Level 1
The baseline Level One emphasises countering malicious actors utilising easily available tactics and tools. The emphasis here is on bolstering basic cyber hygiene practices, such as patching vulnerabilities and enhancing user authentication.
Implementation of proactive measures against common threats, like social engineering and leveraging publicly-available exploits, contributes to minimising potential vulnerabilities.
Level 2
At Level Two, the organisation's efforts concentrate on dealing with adversaries willing to invest more time and expertise. Strengthening cyber defences involves adopting proactive security measures, including phishing prevention, and industrialising authentication safeguards.
The organisation adapts to emerging threats swiftly and effectively, reducing the risk of data compromise, system infiltration, and prolonged unauthorised access.
Level 3
The highest level of maturity targets sophisticated malicious actors with adaptive strategies. The organisation's capabilities evolve to thwart advanced techniques designed to evade detection and circumvent controls. Advanced detection and response mechanisms and implementing comprehensive logging and monitoring, become essential.
This level demands a proactive approach that includes rapid adoption of new security measures, staying ahead of emerging threats, and fostering a culture of cyber resilience.
For context, the Cythera team have developed a visual example here:
Achieving Level 1 Maturity with Cythera's Innovative Solutions
At Cythera, our partnerships with CrowdStrike, Automox and Druva provide practical Essential Eight tooling, with solutions across all eight aspects of the framework. As an Australian Reseller and Managed Security Service Provider (MSSP), we partner with CrowdStrike, Automox and Druva in Australia to assist you in implementing these security platforms for your company. These practical tools help Australian organisations to strengthen their security posture and reach Level 1 maturity and address the majority of Level 2 controls.
This series of articles will focus on the Essential Eight as the convenient starting point to a compliance journey, we welcome you to follow along. If you would like to organise a meeting to discuss our compliance expertise, please contact us today.























